IT Evolution. Ours is an industry in a constant state of flux. As the needs of our managed clients continue to grow more complex, our scalability to meet those needs becomes increasingly obscure and challenging. As the threats around us morph from casual probes into direct assaults, the security landscape we find ourselves in as IT service providers is turbulent and often difficult to keep up with.
There was a time when sharing administrative credentials was an acceptable norm – we had yet to fully grasp the gravity of what it meant to share unfettered and unmonitored access to critical networks and systems. With no policies or procedures in place to control access, dictate privileges, ensure secure credentials, log activity, or disable accounts – we were quite literally passing around the keys to the kingdom to anyone who may have claimed to need them – and no efficient way to take them back or change the locks.
 If we are being honest with ourselves, most of us read that and acknowledge that sharing passwords is probably a bad idea – even if you do it now in some capacity.
If we are being honest with ourselves, most of us read that and acknowledge that sharing passwords is probably a bad idea – even if you do it now in some capacity.
You may feel like you have no other choice at times, or that the convenience outweighs what you perceive as a smaller risk than it actually is. Perhaps you have a band-aid policy in place that attempts to limit/monitor the sharing of passwords, or you use a password storage vault such as Passportal or Last Pass and feel like you’ve checked the box.
But is a vault or a band-aid policy really enough? 2020 saw over 5 billion recorded malware attacks. Often, malicious actors will use malware to steal passwords, access critical systems, and deploy ransomware. And that’s just one example of hundreds of vectors bad actors use to compromise credentials.
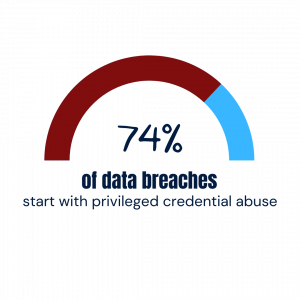
In many cases, it’s as simple as a technician leaving a work station unlocked, or writing credentials down carelessly. Considering 74% of data breaches begin with password abuse, there is simply too much at stake to settle for anything less than a completely holistic approach to privileged account management – passwords are only the tip of the iceberg.
So what is the answer? A unique account for every technician on every domain.
But is this tenable? For this to work, you need to somehow:
- create an account for each tech on all of the existing clients’ networks they need to access, as well as any new clients you may onboard as you grow,
- control the rights and privileges of each account,
- ensure the secure management of their passwords,
- and ultimately – be able to quickly disable accounts in the event of a breach.
But even if I only have 5 technicians and 50 clients, that’s a minimum of 250 accounts – and even if it only took me 3 minutes to change a password for one account, that’s over 12 man hours spent in just changing passwords every 30 – 90 days. What if you had 25 techs and 100 clients? Now you are looking at well over 120 man hours spent in changing passwords alone. This doesn’t even include the time to create/disable accounts, configure rights, or the time associated with finding and entering credentials. Can you imagine changing 2,500 passwords daily?
Enter the solution:
 We deeply understand the need for MSPs to efficiently and effectively manage their technicians’ privileged accounts, and we know you have too many irons in the fire for this platform to be overly-complex, difficult to deploy, or challenging to manage. It needs to be simple, elegant, and effective – and we believe we’ve done it.
We deeply understand the need for MSPs to efficiently and effectively manage their technicians’ privileged accounts, and we know you have too many irons in the fire for this platform to be overly-complex, difficult to deploy, or challenging to manage. It needs to be simple, elegant, and effective – and we believe we’ve done it.
TechIDManager has ushered in a new paradigm in privileged account management.
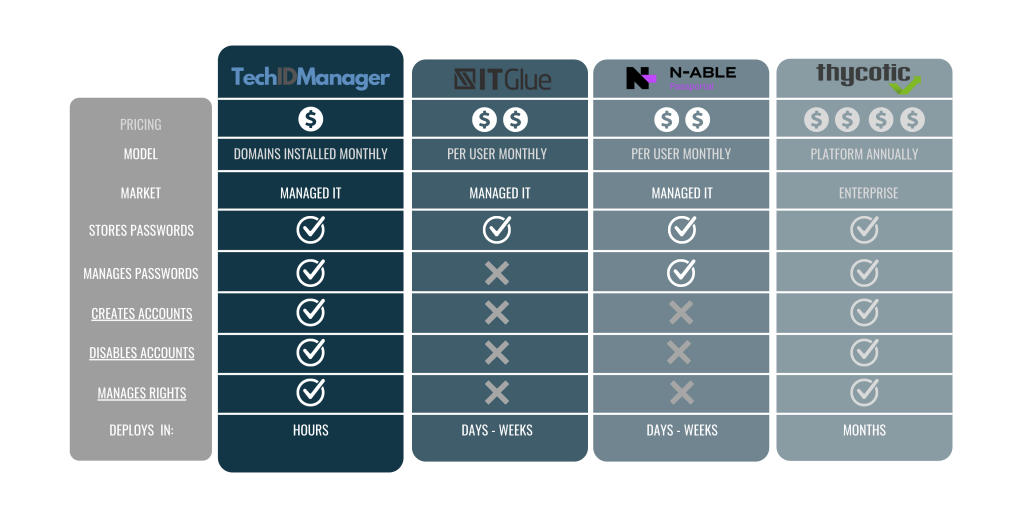
No other platform on the market comes close to addressing this need as directly and holistically as TechIDManager. Below you can see how we stack up against a few common tools we are often compared against.
Ask us to show you a personal demonstration today.