A tale from MSP land
MSP – “What do you mean, ‘everything is down?'”
Client – “I don’t know what to tell you . . . nothing is working!”
MSP – “Have you tri….”
Client – “I’m telling you, I’ve tried everything. Tell me what to do. Please!”
MSP – “I’ll be right over.”
45 minutes later, the technician rolls into his customer’s parking lot.
Client – “Thanks for coming so soon. We’re dead in the water.”
The tech walks by the 25 workstations on his way to the small server room in the back of the office. Bored employees are milling about aimlessly and chatting casually while they wait for the situation to be resolved.
He steps into the unlocked server room and quickly notices something is off.
MSP – “Where is it?”
Client – “What?”
MSP – “Your firewall, where is it?”
Client – “What’s wrong with our firewall?”
MSP – “It’s missing – see?”
he gestures to a rectangular outline framed in dust where the firewall once resided.
Client – “I have no idea!”
Sure enough, someone had stolen the client’s firewall, and there was no way of getting it back.
This story was shared with me recently on a discovery call with an MSP, and it struck me as an incredible reminder – most managed clients are one un-plugged box away from being completely incapacitated.


The pot & the kettle
How did this happen? Was there any social engineering involved? Was it a disgruntled employee? Did a night janitor decide to make a few easy bucks? In this case, we will likely never know.
Of course, this could have easily been prevented. The answer is probably pretty obvious to most of you. You might be thinking something like the following:
- Lock the server room door!
- Ensure there are only two keys (one as a backup secured in a safe).
- Make sure there is a clear policy for who is allowed to use the key, and when.
- Enforce that policy strictly with no exceptions.
- Set up a surveillance camera inside the server room to record anyone coming or going.
We all know how difficult it can be to convince end-users to implement and pay for security measures they don’t think they will ever need, but I would wager this client put a lock on their server room door the very next day!
It can be easy for MSPs to criticize this client for poor security policies in their office, but before you judge them too harshly, I want to ask you a pointed question.
Do each of your technicians have a unique account on every domain they access?
If your answer is anything short of “Yes, absolutely!”, then I have some bad news for you – you are a pot calling the kettle black.
Ever watch The Andy Griffith Show?
Do you remember the episode where a drunk Otis teeters into the Mayberry Sheriff’s office and casually reaches for the keys on the wall right next to his favorite cell?
Yeah, it’s like that. Except that Otis is a goofball, and cybercriminals are highly-intelligent engineers who excel at compromising systems and quietly evading your detection.
Would you even know if an Otis was walking into your client’s domains? If you knew, how difficult would it be for you to get that key away from Otis? How difficult would it be to change all the locks?
Sharing accounts and credentials with multiple techs and across multiple clients is no more secure than leaving a door unlocked, or hanging the key on a peg outside. You’ll never know who is walking in at any given moment. You’ll never know who may have changed, moved, or stolen something. You’ll never know if Otis made himself a copy of the key.
If your technicians are sharing passwords – then you are risking far more than the customer who leaves his server room unlocked. You are not only jeopardizing your own systems and data, but also that of every client you have.
You’re about as secure as the Mayberry Jail!

The siege is real
I shouldn’t have to tell you how real the threat is. Cybercrime has grown into a multi-billion dollar industry, and with the rise of ransom-as-a-service, MSPs have painted a large target square on their backs by the very nature of who they are and what they do.
Ubiquiti
SolarWinds
Kaseya
Names that sting for many MSPs to read about – and those are just to name a few recent, channel-specific instances.
WordPress
Irish Health Care Service
Colonial Pipeline
I won’t wear you out with a list you are already very familiar with, but you get my point.
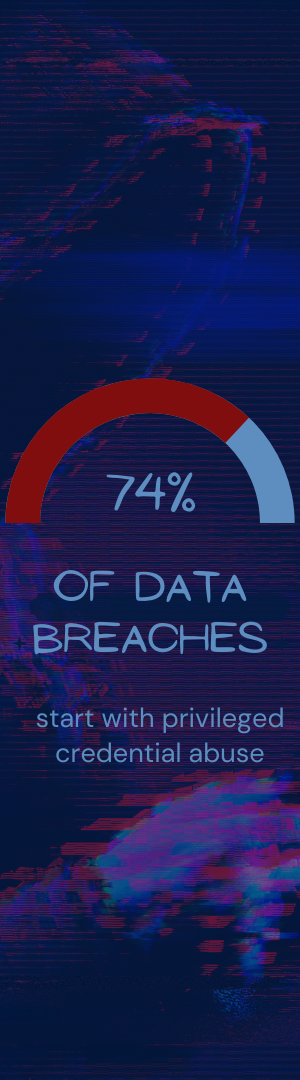
What’s more, according to a study done in 2019, 74% of data breaches begin with privileged credential abuse.
The formidable forces of cybercrime have rallied. They are funded, organized, and deadly – and they are coming for your technicians’ passwords.
If your MSP is a castle, and all of your clients are inside, then privileged accounts are the gates these forces will try to storm and breach.
It’s time to drop the portcullis: